
Cointelegraph Bitcoin & Ethereum Blockchain News
What’s digital identification?
Your digital identification is the fingerprint you permit throughout the web, a dwelling map of who you might be.
Your digital identification is extra than simply your title or e-mail; it stretches out of your social media profiles and crypto wallet addresses to your system fingerprints and even the rhythms of your every day shopping habits. Within the fast-moving world of cryptocurrency, the place identification and monetary entry usually overlap, digital identity theft isn’t only a nuisance; it’s an open door to your property.
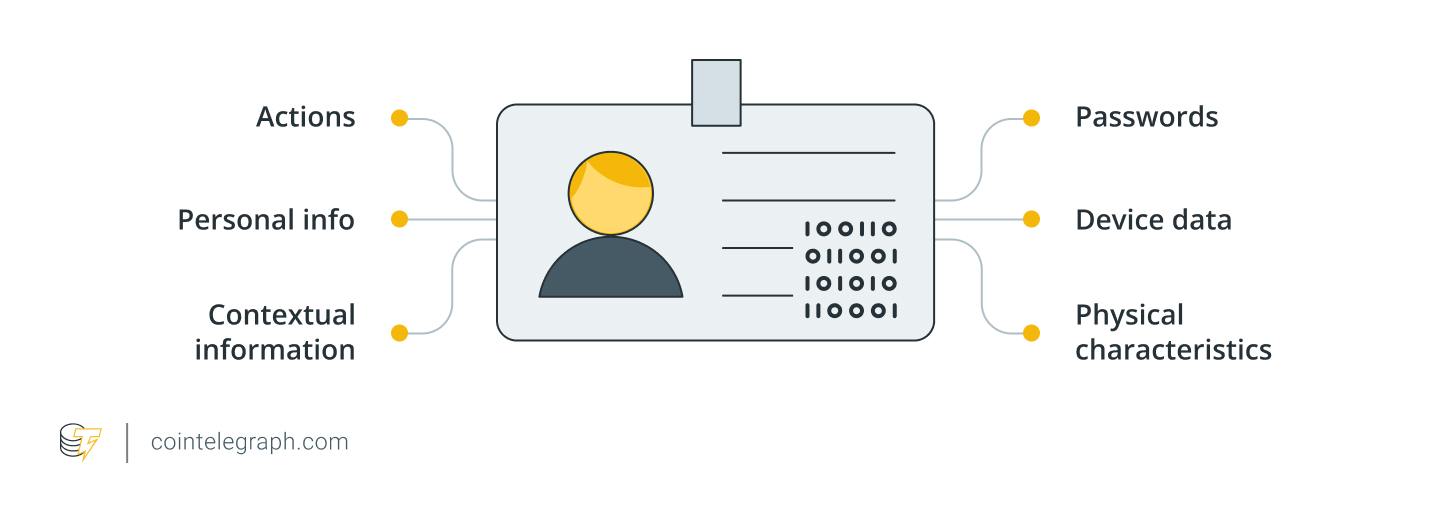
With out sturdy safety, even small items of stolen data may be stitched right into a full profile, giving cybercriminals every thing they should impersonate you, seize your funds or lock you out of your accounts.
What many don’t notice is how shortly this publicity occurs. Each new pockets connection, change login, or saved cost methodology quietly expands your digital floor space. With every step, your information turns into extra invaluable and extra weak. In a panorama the place data is forex, your cyber identification can turn into a jackpot for hackers who know the way to money it out.
Do you know? In 2025, specialists estimate that over 50 billion digital identities might be compromised worldwide, a 22% bounce from final 12 months. Crypto customers are among the many largest targets, particularly on decentralized finance (DeFi) platforms with out sturdy identification checks. Artificial identification fraud can also be exploding, hitting new crypto lending companies the toughest.
How cybercriminals steal your digital identification
Cybercriminals mix know-how and manipulation to pry open digital identities.
Phishing stays a standard entry level, the place faux web sites or emails trick customers into revealing passwords or seed phrases. Massive private information breaches leak databases of usernames, emails and credentials, fueling account takeover assaults throughout totally different companies.
Hackers additionally exploit:
- Artificial identification fraud: combining actual and pretend information to create new identities.
- Social engineering assaults: manipulating users emotionally to voluntarily reveal delicate data.
- Credential stuffing: utilizing leaked passwords on different platforms, hoping customers reused them.
Figuring out how criminals exploit crypto markets and digital ecosystems could make it a lot tougher to be tricked.
Stolen identification, bought eternally on the darkish net
As soon as your information is stolen, it usually finally ends up on the market on the darkish net, multiplying the risk.
Darkish net identification theft is a thriving economic system. Full identification profiles, together with names, emails, Social Safety Numbers (SSNs) and crypto keys can fetch excessive costs. Patrons could use the stolen identification instantly or resell it repeatedly, creating a number of waves of assaults months and even years later.
Even after you lock down your accounts, your leaked information can maintain circulating in darkish corners of the net. That’s why instruments like darkish net monitoring and breach alerts aren’t elective; they’re your long-term protection. Restoration isn’t a one-time repair. It’s a behavior of staying alert and adapting.
Indicators your digital identification has been stolen
Recognizing the indicators of identification theft early can cease criminals earlier than they trigger main harm.
Victims of cyber identification theft could discover unusual transactions, denied logins or units showing that they do not acknowledge. Typically the indicators are monetary — unauthorized bank card fees, modifications in your crypto balances or sudden loans beneath your title.
Key warning indicators embrace:
- Password reset requests you didn’t provoke.
- Locked-out accounts or sudden logouts throughout units.
- New accounts or credit score traces showing in your monetary historical past.
- Surprising withdrawals or transfers from crypto wallets.
By catching the indicators of identification theft early, you may shut down fraud earlier than it spirals, and shield your cash and your title.
What to do in case your identification is stolen
Quick, clear motion provides you the perfect probability to restrict the harm from identification theft.
Should you notice your identification has been stolen, the primary precedence is locking down entry. Replace your passwords throughout all platforms, allow two-factor authentication (2FA) safety, and revoke entry to any suspicious classes or units. Most main exchanges, banks and crypto companies let you briefly freeze your accounts whilst you examine.
Past rapid safety steps, you must report the incident to authorities and file a case together with your native cybercrime unit or monetary safety company.
Utilizing on-line assist companies can pace up your response plan. These preliminary strikes by means of clear restoration steps are vital to regaining management earlier than criminals unfold the assault additional.
Restoration steps after digital identification theft
Recovering from identification theft includes extra than simply securing your passwords; it’s an entire rebuild of your digital belief.
After locking down your accounts and alerting key establishments, it’s essential begin lively monitoring. This implies recurrently reviewing your financial institution statements, checking your crypto wallets for unauthorized transactions and inspecting your credit score report for any new exercise.
Some victims additionally pursue:
- Submitting fraud alerts or credit score freezes with main credit score businesses.
- Hiring skilled identification restoration companies.
- Exploring identification theft insurance coverage to cowl authorized and investigative prices.
Full restoration can take months, however a scientific method reduces monetary and emotional harm.
The best way to shield your digital identification
Good safety habits are the strongest protection in opposition to cybercriminals.
Crypto platforms and firms ought to undertake decentralized blockchain-based identity solutions. These techniques be certain that your information stays safe, clear and in your management, making it a lot tougher for hackers to govern or steal your private data.
In contrast to centralized techniques, blockchain-based identities are saved on a distributed ledger, lowering single factors of failure and making it considerably harder for cybercriminals to realize unauthorized entry. Moreover, decentralized identification techniques allow customers to confirm their identities with out exposing delicate private information, permitting for extra privateness and management over who sees their data.
For customers, fortifying their digital identification isn’t about ticking packing containers; it’s about constructing sharp habits that evolve with the dangers. Right here’s the way to keep forward:
- Deal with passwords like armor: Use sturdy, distinctive combos for each account. A password supervisor can forge and guard them higher than reminiscence ever may.
- Double down with 2FA: One password isn’t sufficient, so add an additional lock on each door price defending, particularly your funds and crypto.
- Observe digital minimalism: Each birthday, pet title or picture shared on-line can turn into ammo for hackers.
- Select sensible allies: Persist with crypto platforms that prioritize decentralized digital identity verification and actual safety, not simply flashy guarantees.
- Watch, detect, reply: Set alerts and monitor your accounts. Recognizing unusual exercise early can flip a catastrophe into an in depth name.
- Be stingy together with your information: Solely belief platforms that accumulate the naked minimal. If a web site asks for an excessive amount of, stroll away.
- Keep away from straightforward errors: Public WiFi is a hacker’s playground. Use a VPN while you join, and recurrently examine in case your credentials have leaked.
The much less you reveal, the safer you keep.
Replace, overview, repeat: Your digital identification relies on it
Sustaining your digital identification is a every day observe, not a one-time setup.
Often replace your passwords and safety settings. Evaluation app permissions, system authorizations and pockets connections at the very least each few months. Incorporating biometric authentication (fingerprints or facial scans) provides a vital bodily layer of safety past passwords.
Understanding how hackers manipulate crypto — from phishing for personal keys to setting traps with faux decentralized applications (DApps) — is what retains you a step forward. In as we speak’s world, staying sharp about cybersecurity isn’t elective. It’s a fundamental survival talent, proper up there with managing your cash or defending your private home.
The longer term will solely turn into extra digital and extra decentralized. Defending your digital identification as we speak means preserving your independence tomorrow.









